Rian Booyer
Instructor Rick Powell
CISS 280 ADE – Systems Analysis & Design I
04 April 2017
Wireless Security and Its Importance
Security is an important part of wireless networking. Without proper network security people, could easily steal client information or abuse the network resources. This could even expose businesses to litigation due to their network being used for illegal purposes. Even before the wireless network integration is decided upon. The analyst needs to take security seriously during the planning stage and decide on what they want to provide access to for the specific wireless network and its possible clients. Let’s take the example of a public wireless connection used in a library. The public wireless network would benefit from wireless isolation, VLAN setup or even a combination of the two. If the wireless network is for a business, separating clients into VLANS restricts access to specific resources based on the organizations structure, increasing security. We will be discussing several sections on wireless security and some of what goes on behind the scenes.
Service Set Identifier (SSID)
An SSID is one of the most basic pieces of security for a wireless access point or router. The SSID is “a case sensitive, 32 alphanumeric character identifier attached to the header of packets sent over a wireless local area network” (6). A client trying to access a wireless network must have this identifier to even begin the process of authenticating to the wireless network. Without the SSID there is no hope of connecting. Most wireless networks in use today broadcast the SSID openly to allow clients easier access to the network. This is useful for open public access points; however, within a business it could offer a possible security threat. One easy way to start securing your network is to not broadcast the SSID openly, but setup the SSID manually on devices wishing to connect to the network (6).
Wireless Equivalent Privacy (WEP)
WEP security was better than nothing in its day. WEP was the first security standard offered for wireless networks and developed by IEEE (3). WEP keys were hexadecimal (0-9, A-F) pre-shared set of four keys generated from a passphrase. Those four keys were switched many times to try and make it more difficult for a hacker to “sniff” the key from packets being broadcast to the access point. Without the four keys a hacker would have an easier time detecting the network key in use and breaking into the system. The network administrator would have to manually enter the key into each client that wanted to access the network. Many older wireless systems used WEP as their standard without any other security types available (3). My experience started with 802.11b cards that seemed to exclusively use WEP encryption. Later in my career, better encryption was released and the software was updated and integration of more secure solutions that had better security options such as WPA-PSK using TKIP and eventually WPA2-PSK using AES encryption became possible.
Temporal Key Integrity Protocol (TKIP)
TKIP is similar to WEP, but it acts as a “wrapper” encapsulating the WEP security in additional algorithms at the “beginning and end to encapsulate and modify it” (2). It was originally designed to allow clients to upgrade their security on their wireless networks without replacing their legacy equipment. The TKIP wrapper encrypts each packet with a unique key that is much stronger by implementing additional algorithms than the ones used in standard WEP encryption. TKIP is still offered on many routers today for backwards compatibility with older equipment (2).
Advanced Encryption Standard (AES)
Advanced Encryption Standard (AES) is a type of block cipher used in many of todays’ wireless devices. It was originally developed by the United States Government to protect classified information (1). Development of AES encryption started in 1997 by the National Institute of Standards and Technology (NIST) as a successor for the Data Encryption Standard (DES). The AES protocol uses 128, 192, or 256-bit encryption. Older wireless routers and access points that had the option for AES in my experience only gave you the choice of only 128 bit or 256-bit encryption (1). Many Small Office Home Office (SOHO) routers and access points today provide AES for security on them while some still providing TKIP through WPA and AES through WPA2 using pre-shared keys.
Wireless Protected Access (WPA)
Wireless Protected Access (Technically Wi-Fi protected access) first introduced in 2003 is offered in multiple forms. First off you have WPA-PSK and WPA2-PSK also known as WPA/WPA2 Personal. These methods use a pre-shared key either in TKIP (WPA) or the more advanced AES (WPA2) algorithms to encrypt data between wireless devices (4). Another standard meant for businesses is the WPA/WPA2 Enterprise, which uses 802.1x authentication through a Remote Authentication Dial In User Service or RADIUS server or a type of server called Authentication, Authorization, and Accounting server or AAA (5, Page 2). With the Enterprise standard, the wireless access point must exchange a “secret” key for authenticating to the RADIUS server for access to the network, but also has to pass along the clients’ secret key to the RADIUS server to allow the client to connect and authenticate on the network (5). This is good in an enterprise environment to prevent unauthorized computers from gaining anonymous network access.
For this I am going to use an example that shows how a wired access protocol could benefit a business with WPA/WPA2 enterprise and a RADIUS proxy server for IP address assignment. The average client accesses the network authenticating through the 802.1x servers to gain access not only to the network but to request assignment of an IP address to their device. Bob, however, wants to gain access wirelessly to bypass security from outside the office and to obtain access to secured network resources. He fortunately does not know the secret keys the RADIUS server is setup to use. Bob uses an open RJ-11 port to plug in a wireless access router. The router tries to get on the network, but since it doesn’t have access to the 802.1x server key’s it is not assigned an IP preventing network access. However, even though this works, if the administrators were using MACSec security on their wireless network the wireless access router would have no access at all.
Smart Cards, USB tokens and software token authentication
For this section I only have Wikipedia as a source, it’s not usually allowed but finding specific information wasn’t available except from manufacturers websites. Smart cards, USB tokens and software tokens seem to be the new standard for the strongest security for wireless networks. They work by using an internal code embedded into the device (smart card, usb or software token) to create a “powerful algorithm” that generates a new encryption code every time the token is used. A simple final explanation from Wikipedia (I can hear all the boo’s out there) is:
“The server will be time synced to the card or token. This is a very secure way to conduct wireless transmissions. Companies in this area make USB tokens, software tokens, and smart cards. They even make hardware versions that double as an employee picture badge. Currently the safest security measures are the smart cards / USB tokens. However, these are expensive. The next safest methods are WPA2 or WPA with a RADIUS server. Any one of the three will provide a good base foundation for security.” (15)
Wireless Isolation
Wireless isolation is offered on most business access points and routers as well as many consumer devices. Wireless isolation allows the administrator of the network to “isolate” clients from using anything on the connected wired network as well as not being able to access any other wireless clients connected to the same network. The isolated clients will still have access to specific services such as the internet (7).
Without wireless isolation, the connected clients are considered a part of the same local network and are treated with the same access as that on a local network. They also have access to the wired network resources that an administrator might not wish them access to. (7)
Wireless isolation is especially useful in public access situations where anyone, such as a library, can connect. The library would have an “open” network with no security so their patrons can surf the web, check email, access online library resources, shared public printers and much more. Bob, however, being the rascal he is wants to wirelessly sniff packets and capture network traffic to try to steal things such as usernames and passwords from the other clients. Remember there is no encryption on the network such as WEP, WPA, WPA2, so the data is unencrypted. It would be easy for Bob to capture those packets and later search them for the data he wishes to find. If wireless network isolation was turned on it would make it much more difficult for him to capture the packets from other clients. Bob also wouldn’t have access to any wired resources to try and hack the servers or staff computers.
MAC Security (MACSec) and filtering
Media Access Control address or MAC address is a collection of hexadecimal characters that identify a network device. Every network device is assigned a unique MAC address at the manufacturer that cannot be changed (8). Specifics on the MAC address are beyond the scope of my paper but if you need more information please check out reference 9 below (19).
There are some devices that allow you to alter the MAC address using a software interface. Several devices, mainly motherboards with onboard wired network interfaces, allow you to specify a custom MAC address inside the onboard BIOS. This causes problems with MAC security and filtering because some clients can easily get MAC addresses off the network by using a simple non-administrator command prompt in windows and running the command arp -a which displays the MAC addresses the computer has registered in the arp database. The administrator of the network, as a good practice, should block access to the command prompt or terminal, and set security associations on specific commands to help prevent giving out information that could possibly be used to gain unauthorized access to network resources.
Filtering by MAC address uses an Access Control List (ACL) on the router to either allow or deny devices access to the network, and with more modern wireless access points and routers they allow you not only to specify wireless access lists but wired access lists. The Netgear R6400 is a good example of a newer wireless router that also allows blocking of wired devices on the network using an Access Control List (19).
For example, let’s talk about Bob again. When Bob tries to connect the wireless router into the network that uses MAC security access lists to maintain a list of allowed devices. The network router checks the MAC address for the access point Bob plugs into a wired wall port and denies access because the router does not recognize the devices MAC address and rejects the connection. If Bob is smart enough though he could mirror a known MAC address if the access point allows the user to change the MAC using built in software or a custom firmware downloaded from certain sources.
Restricting access by schedule
Many modern wireless access points and routers provide the option to restrict access to the network by an actual time schedule. This option can be setup to only allow specific days and times for access. Some more expensive routers and access points have the option of setting up the schedule by MAC addresses if you don’t want specific clients on at certain times. This would benefit many organizations or businesses by limiting access to the hours they are open or by limiting a specific group to the times they should only have access (14).
Wireless Virtual Local Area Networks (VLANS)
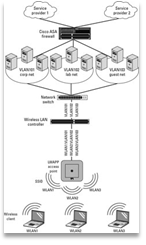
VLAN network (10)
VLANS have the capability of isolating wired or wireless connections to a “virtual” portion of the network. While the client is connected to the VLAN they only have access to the specific devices and services that the administer specified for that virtual network (10).
For example, a public library could use a VLAN that isolates all wireless clients to a virtual network that gives them access to the internet, a printer, and scanner. The main office computers on another VLAN that gives them access to the employee network infrastructure, and the administrative network would be isolated from both to keep sensitive information secured. Almost 15 years ago this wasn’t a cheap thing to do and most organizations would either just try to lock down network resources the best they can or just create a system that had multiple network infrastructures which not only requires high initial costs but also high costs to maintain the system.
Content Filtering and relation to wireless networking
Content filtering is highly important for schools, libraries, and businesses that need or are required to use it. Network users sometimes decide to try to access undesirable information such as hate crimes, pornogoraphy, and waste time on social media. One of the easiest ways is to setup content filtering that checks what the clients are requesting and blocks them if the admiration decides that they shouldn’t be on specific sites or services. Some businesses use content filtering to restrict access to social networking sites such as Facebook and Twitter to try to keep employee’s working instead of talking to their friends all day. (11)
From my personal experiences at a library content filtering uses a service provider such as iBoss and Netsweeper that goes through web addresses and labels them into categories that can be blocked by the local administrator. The administrator chooses the categories or specific sites to allow and block on the network. When a client tries to access a website, or service the request is forwarded to the service provider by a router and would receive a response to either block or allow the request. Most large libraries and businesses use local servers that sync the database of URL addresses from the service provider at specific intervals and instead of forwarding the request to the provider it forwards the information to the internal servers improving the performance and can also allow the system to perform its function even if the service providers systems are temporarily unavailable to handle requests.
HTTPS filtering
HTTPS filtering can be considered a sub-function of content filtering. HTTPS filtering is used by many public entities and businesses to block sites that are encoded using Secure Socket Layering which causes problems for the content filtering to detect possible security problems. These problems could range from vulnerabilities such as malware, viruses, to software that could possibly harm network resources. Administrators waste a lot of time trying to either detect or repair these security problems and to save money and lost hours they decide to block all HTTPS access. Since HTTPS is encrypted it is hard for security software to catch the “problems” that some sites try to maliciously slip onto computer systems. HTTPS filtering can be setup multiple ways to either block all HTTPS sites and services on the internet, or with specific filters, the system can decode the encrypted page, check the information, then re-encode the page and send it to the user (13). Modern search engines, specifically Google, penalizes web pages that use http instead of https because they wish for the internet to be more secure (12).
RF shielding for buildings
RF shielding works by attenuating the wireless signal so that it cannot pass outside of the confines of your building (or section of a building), to help prevent unauthorized access.
RF shielding takes on multiple forms, it can be as simple as a special type of paint used on your walls and special window film that reduces the signal, to building actual Faraday cages into the walls of the building (18).
Most wall paints and window films will attenuate the signal between “40dB to 80dB” while a Faraday cage will attenuate the signal depending on how complicated the actual cage is designed. Faraday caged walls are usually too expensive for smaller organizations to implement so they usually use the paint method which is considerably more cost effective to implement (18).
Hospitals are one type of organization that commonly uses RF, ionizing radiation, and other types of shielding to block unwanted signals inside the hospital. The types of RF and radiation they shield against range from X-rays to general wireless signals generated anywhere from the 900mhz band to the 5ghz band where many cell phones and wireless devices operate and can cause problems with their internal equipment (18).
Conclusion
My past experiences with wireless security has helped a lot with writing this paper. At home I have had to implement some, but thankfully not all of, these security protocols for my home network. I personally use a non-broadcasting SSID, WPA2-psk personal and MAC filtering. The reasoning for this is because at one time I didn’t secure my network with the MAC filtering and a visiting kid could pull the configuration information including the password from his computer then accessed my network from outside the house and downloaded fifteen files that violated the DMCA, my internet provider was not happy.
When I worked for the library, many of these options for security were not available at the time. We were basically starting out with an old 802.11b network with very basic routers. We used a WEP key that we changed every day; patrons would have to ask for it which annoyed them to no end. My solution for someone just driving up after hours with that day’s key and, well doing things they shouldn’t be, was to install a basic light switch that controlled the device that injected Power Over Lan for the routers. After hours the librarians just switched the equipment off on their way out thinking the switch was just another light.
Works Cited
- Rouse, Margaret “Advances Encryption Standard (AES)” Techtarget.com,
http://searchsecurity.techtarget.com/definition/Advanced-Encryption-Standard, Accessed 5 April 2017. - Rouse, Margaret “TKIP (Temporal Key Integrity Protocol)” techtarget.com, http://searchmobilecomputing.techtarget.com/definition/TKIP ,Accessed 5 April 2017
- “What is a WEP Key?”, lifewire.com, https://www.lifewire.com/what-is-a-wep-key-818305 , accessed 5 April 2017
- “Understanding WPA-PSK and WPA2-PSK Authentication” juniper.net, https://www.juniper.net/techpubs/en_US/network-director1.1/topics/concept/wireless-wpa-psk-authentication.html , Accessed 5 April 2017
- Geier, Eric “moving to WPA/WPA2-Enterprise Wi-Fi Encryption” ciscopress.com, http://www.ciscopress.com/articles/article.asp?p=1576225 , Accessed 5 April 2017
- Beal, Vangie “SSID – Service Set Identifier” webopedia.com, http://www.webopedia.com/TERM/S/SSID.html , Accessed 5 April 2017
- Hoffman, Chris “Lock Down Your Wi-Fi Network With Your Router’s Wireless Isolation Option” howtogeek.com, https://www.howtogeek.com/179089/lock-down-your-wi-fi-network-with-your-routers-wireless-isolation-option/ , Accessed 5 April 2017
- Fitzpatrick, Jason “What Exactly Is a MAC Address Used For?”, howtogeek.com, https://www.howtogeek.com/179089/lock-down-your-wi-fi-network-with-your-routers-wireless-isolation-option/ , Accessed 5 April 2017
- “Introduction to MAC Addresses” lifewire.com, https://www.lifewire.com/introduction-to-MAC-addresses-817937, Accessed 6 April 2017
- Tetz, Edward “Wireless Network Security: Isolating Users With Vlans”, dummies.com http://www.dummies.com/programming/networking/cisco/wireless-network-security-isolating-users-with-vlans/ , Accessed 6 April 2017
- Rouse, Margaret “Content Filtering (information filtering)”, techtarget.com, http://searchsecurity.techtarget.com/definition/content-filtering , Accessed 6 April 2017
- “Google to Prioritize the indexing of HTTPS Pages”, searchenginejournal.com, https://www.searchenginejournal.com/google-to-prioritize-the-indexing-of-https-pages/147179/ , Accessed 6 April 2017
- “ HTTPS Content Filtering Solution”, webtitan.com, https://www.webtitan.com/https-content-filtering-solution/ , Accessed 6 April 2017
- “Setting Up Access Restrictions on a Linksys router using the classic web-based interface”, linksys.com, http://www.linksys.com/ph/support-article?articleNum=136710 , Accessed 6 April 2017
- “Wireless Security” Wikipedia, https://en.wikipedia.org/wiki/Wireless_security#Smart_cards.2C_USB_tokens.2C_and_software_tokens , Accessed 6 April 2017
- Geier, Jim “How to: Improve Wireless Security and Performance with Shielding” wireless-nets.com, http://www.wireless-nets.com/resources/tutorials/rf_shielding.html , Accessed 6 April 2017
- Scarpati, Jessica, “Wireless Security Protocols: The difference Between WEP, WPA, WPA2” techtarget.com, http://searchnetworking.techtarget.com/feature/Wireless-encryption-basics-Understanding-WEP-WPA-and-WPA2 , accessed 6 April 2017
- “Shielding in buildings” archtoolbox.com, https://www.archtoolbox.com/representation/architectural-concepts/shielding-in-buildings.html , Accessed 6 April 2017
- “How do I configure Access Control or MAC Filtering on my router using the NETGEAR genie user interface?” Netgear, https://kb.netgear.com/23289/How-do-I-configure-Access-Control-or-MAC-Filtering-on-my-router-using-the-NETGEAR-genie-user-interface?cid=wmt_netgear_organic , Accessed 6 April 2017.